Stripe CTF: Level #1
Posted on sam. 13 octobre 2012 in Write-up

You can find the code of this level here.
(sha256: b67c313a1a3bebd8702159efae32f95f1b41885f6e00103ee53e896a53194f43)
So, this level wants you to guess a password, stored in a file named "secret-combination.txt" on the server. If you manage to do it, it'll give you the password for this level. Let's take a look at the code and see how to get the password without knowing the combination.
The server starts by defining a variable $filename equal
to "secret-combination.txt". That's the file of the combination (I'm so
deductive). It then retrieves your attempt (which was passed by GET),
and compares it to the content of the file. If they're the same, the
server will gives you the sweet, sweet password. Otherwise, tough.
The thing is, the server doesn't retrieve your attempt using
$_GET['attempt']. It uses the extract PHP
function on the
$_GET array. Basically, for every entry $_GET['key'] = value,
it’ll create a variable $key with the value
value. It means that if we give a parameter filename in the
GET request, we can override the variable $filename, and open
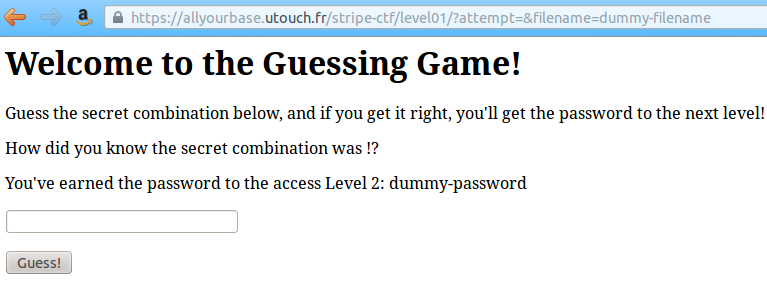
any file. So let's open a non-existing file, and give an empty guess:
?attempt=&filename=dummy-filename.txt
This request will set $filename to "dummy-filename.txt", so
that when the server tries to retrieve its content, it'll yield an empty
string. Since our attempt is empty, it will match, and the server will
give us the password for this level.
w00t!